Three-Tier Web Architecture
Designed a scalable three-tier web app using ALB, EC2 Auto Scaling, and Amazon RDS. Built to simulate production architecture with layered separation of frontend, backend, and database.
7/16/20252 min read
Introduction
For any growing web application, separating responsibilities across frontend, backend, and database layers is a best practice that ensures scalability, flexibility, and maintainability. In this project, I built a production-grade three-tier architecture on AWS that mimics how modern enterprise apps are deployed in the cloud.
The architecture is inspired by a real-world use case I implemented for a mid-size business, helping them move away from a monolithic, single-server deployment to a modular and scalable setup.
Project Goals
Separate frontend, application logic, and database layers
Ensure high availability and fault tolerance
Use scalable AWS services like Auto Scaling and RDS
Learn and apply security best practices for cloud deployments
Reflect architecture seen in large-scale production environments
Frontend Layer
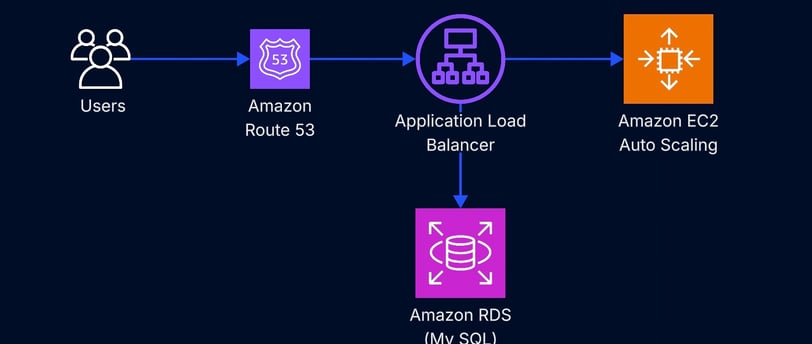
For the presentation layer, I deployed a simple static or dynamic web interface (HTML/CSS/JS or PHP) to a fleet of EC2 instances behind an Application Load Balancer (ALB).
ALB distributes incoming traffic evenly across instances
Instances are launched in an Auto Scaling Group across multiple Availability Zones
Apache/Nginx serves the static files or dynamic templates
While in modern systems this could be handled by S3 + CloudFront, I deliberately chose EC2 to simulate a legacy frontend environment common in many business workloads.
Application Layer
The application logic runs on the same EC2 instances in this setup (tightly coupled), but is structured to be abstracted into a dedicated backend tier in future iterations.
Could support Node.js, Python Flask, or Java Spring apps
Handles form submissions, API calls, session logic
Talks directly to the Amazon RDS database using IAM-authenticated connections or credentials stored in EC2 Parameter Store
This design keeps the backend extensible — future improvements could isolate it into containers or Lambda-based microservices.
Database Layer
The data tier is powered by Amazon RDS running MySQL:
Multi-AZ deployment for high availability
Automatic backups, snapshots, and failover
DB subnet group places RDS in private subnets for security
Connected securely to EC2 via Security Groups and VPC routing
This allowed the business to eliminate self-managed MySQL servers while gaining automated failover, scaling, and monitoring.
Networking & Security
All components are deployed inside a custom VPC with:
Public subnets for ALB and EC2 instances
Private subnets for RDS database
NAT Gateway for EC2 to reach the internet securely (e.g., updates)
Security Groups:
ALB allows inbound HTTP/HTTPS
EC2 only accepts traffic from ALB
RDS only accepts traffic from EC2
This enforces least-access design and isolates sensitive services.
Monitoring & Logging
To keep tabs on system performance and failures, I integrated:
Amazon CloudWatch for EC2 metrics, alarms, and custom logs
ALB access logs to S3
RDS Enhanced Monitoring for real-time CPU, memory, and connection tracking
These logs can be later extended to build a centralized monitoring dashboard or trigger alerts via SNS.
Infrastructure Deployment
Initial deployment was completed manually through the AWS Console and AWS CLI, which helped build a deeper understanding of resource dependencies. I’m currently migrating this stack to AWS CDK to define:
VPC architecture
Auto Scaling Group and ALB
RDS instance and parameter groups
Security groups and IAM roles
This transition to IaC ensures repeatability and automated recovery.
Lessons Learned
Learned to properly segment a VPC using public and private subnets
Understood ALB listener rules, health checks, and target groups
Gained experience configuring EC2 scaling policies
Hardened architecture using Security Groups, IAM roles, and private networking
Saw firsthand how modular architectures improve operational flexibility
Real-World Application
This architecture was modeled after an implementation I designed for a mid-size company transitioning from a single shared server to a layered, cloud-native environment. It enabled them to handle more web traffic, introduce role separation between teams, and prepare for eventual containerization or serverless migration.
Conclusion
Three-tier architecture is a foundational pattern in cloud architecture. It balances separation of concerns, scalability, and control. This project gave me real hands-on experience with AWS compute, networking, database, and security services — all of which are crucial for real-world deployments.
🛠️ Tech Stack:
Amazon EC2
Application Load Balancer (ALB)
Auto Scaling Group
Amazon RDS (MySQL)
Amazon VPC
Amazon CloudWatch
IAM Roles & Security Groups